There are reports of infections in 99 countries, including Russia and China.
Among the worst hit was the National Health Service (NHS) in England and Scotland.
The BBC understands about 40 NHS organisations and some medical practices were hit, with operations and appointments cancelled.
The malware spread quickly on Friday, with medical staff in the UK reportedly seeing computers go down "one by one".
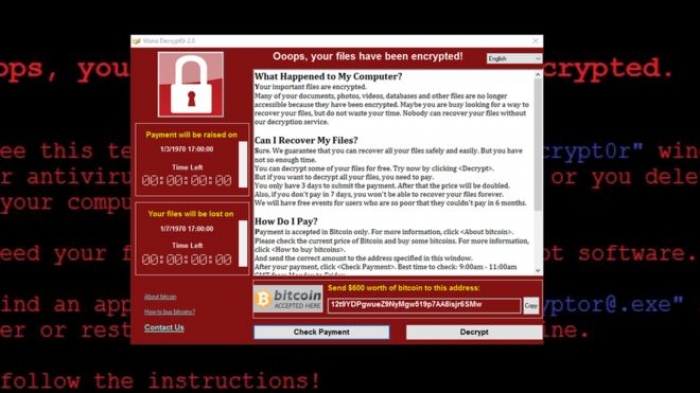
NHS staff shared screenshots of the WannaCry programme, which demanded a payment of $300 (£230) in virtual currency Bitcoin to unlock the files for each computer.
Throughout the day other, mainly European countries, reported infections.
A number of large Spanish firms - including telecoms giant Telefonica, power firm Iberdrola and utility provider Gas Natural - were hit, with reports that staff at the firms were told to turn off their computers.
People tweeted photos of affected computers including a local railway ticket machine in Germany and a university computer lab in Italy.
Portugal Telecom, the delivery company FedEx and a Swedish local authority were also affected.
Some reports said Russia had seen more infections than any other single country. Domestic banks, the interior and health ministries, the state-owned Russian railway firm and the second largest mobile phone network were all reported to have been hit.
Russia's interior ministry said 1,000 of its computers had been infected but the virus was swiftly dealt with and no sensitive data was compromised.
China has not officially commented on any attacks it may have suffered, but comments on social media said a university computer lab had been compromised.
The infections seem to be deployed via a worm - a program that spreads by itself between computers.
Most other malicious programmes rely on humans to spread by tricking them into clicking on an attachment harbouring the attack code.
By contrast, once WannaCry is inside an organisation it will hunt down vulnerable machines and infect them too.
This perhaps explains why its impact is so public - because large numbers of machines at each victim organisation are being compromised, the BBC's technology reporter Chris Baraniuk says.
Some experts say the attack may have been built to exploit a weakness in Microsoft systems that had been identified by the NSA and given the name EternalBlue.
The NSA tools were stolen by a group of hackers known as The Shadow Brokers, who then attempted to sell the encrypted cache in an online auction.
They then made the tools freely available, releasing a password for the encryption in April saying it was a "protest" about US President Donald Trump.
At the time, some cyber-security experts said some of the malware was real, but old.
A patch for the vulnerability was released by Microsoft in March, which would have automatically protected those computers with Windows Update enabled.
Microsoft said on Friday it would roll out the update to users of older operating systems "that no longer receive mainstream support", such Windows XP, Windows 8 and Windows Server 2003.
This means the NHS - which largely still uses Windows XP - can now protect itself from this attack at no extra cost, reports the BBC's North America technology reporter Dave Lee.
A UK-based cyber-security researcher, tweeting as @MalwareTechBlog, said he had accidentally managed to temporarily halt the spread of the virus.
He was quoted as saying that he noticed that the virus was searching for a web address that had not been registered. He bought the domain name for around $10 and found that by registering it, he triggered a "kill switch" that stopped the worm's spread.
But, he warned it was likely to be only a temporary fix.
"So long as the domain isn't removed, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again," he tweeted.
Vikram Thakur, a research manager with security software maker Symantec, told Reuters news agency that there had been a noticeable slow down in the spread of the virus.
"The numbers are extremely low and coming down fast," he said, but warned that could change if the original coding for the virus is changed.
More about: #cyberattack