Chrome updates in the background, so users can usually just relaunch the browser to install the latest version. To manually update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a "Relaunch" button. New-to-Chrome users can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six or seven weeks. It last upgraded the browser on May 27.
Turns on 'Not Secure' warning
The biggest change to Chrome with the debut of version 68 was the new warning labels set into the address bar. While sites whose traffic is encrypted - marked by the HTTPS at the beginning of the URL - will be marked as "Secure," those transmitting data via the unencrypted HTTP will be tagged as "Not Secure."
This campaign of Google's to call out HTTP websites as unsafe began four years ago, with incremental steps toward that goal since. In January 2017, for example, Chrome 56 shamed pages that didn't encrypt password or credit card form fields with the "Not secure" label.
This latest move will not be the last, Google has promised. In early September, with Chrome 69, the browser will remove the "Secure" tag from sites using HTTPS so that encrypted traffic is considered the default. Google's 180-degree turn from browsers' decades-long signage - marking secure HTTPS sites, usually with a padlock icon, to indicate encryption and a digital certificate - to labeling only those pages that are insecure, will wrap up this year. In October, with the launch of Chrome 70, the browser will tag HTTP pages with a red "Not Secure" marker when users enter any kind of data.
As usual, Google adds APIs and plugs security holes
Chrome 68 sports some behind-the-scenes newness as well, which is standard for the browser's updates.
Google highlighted several new APIs (application programming interfaces) in notes to developers, including the Page Lifecycle API and the Payment Handler API.
The former API, Page Lifecycle, offers site and web app developers a way to restore a tab that, for performance reasons, had previously been "frozen" by the browser to conserve resources, including memory and processor load. When the user then returns to the tab, it can be resumed as if nothing had happened.
Payment Handler, on the other hand, lets web-based payment app makers tie into the already-available online checkout infrastructure built into Chrome.
Google also patched 42 security vulnerabilities in version 68, including five marked as "High," the second-most serious ranking in the company's four-step system. Google shelled out $21,500 to researchers for reporting 19 of the bugs, with several bounties still to be decided.
Chrome's next upgrade, version 69, will start reaching users the week of Sept. 2-8.
Google this week released Chrome 66 for Windows, macOS and Linux, patching 62 vulnerabilities, banning older site certificates issued by security giant Symantec, and refusing to run auto-play content unless the volume was muted.
Chrome updates in the background, so users only need relaunch the browser to install the latest version. (To manually update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a "Relaunch" button.) Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six or seven weeks. It last upgraded the browser on March 6.
While some Chrome upgrades, like version 65, are almost entirely about under-the-hood changes, others feature oh-so-obvious new functionality. Still other upgrades boast a mix-a-lot blend of the two. Chrome 66 is definitely in that third camp.
The most visible Chrome 66 enhancement is the arrival of Google's long-discussed ban on auto-play content that dared blare sound from the speakers. Chrome's blockade of such content was first announced last year, when version 64 was to debut the feature. But the mandate did not go live in January, as expected, nor in March with Chrome 65. The ban has finally been made the default in Chrome 66.
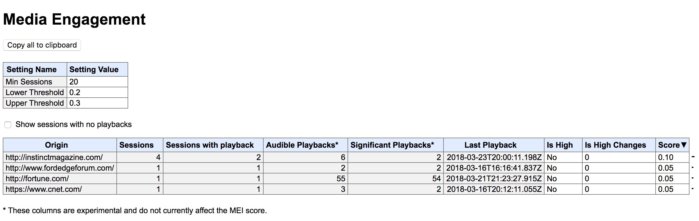
Some exceptions apply: If the user clicks or taps (desktop or mobile, respectively), "somewhere on the site during the browsing session," the audio will play. On personal computers, Google tracks behavior and "if the user has frequently played media on the site, according to the Media Engagement Index" (MEI), audio will play. The MEI, according to a Google explanatory document, "provide[s] a metric reflecting the engagement of a given user with regards to media playback on a given origin." The goal, said Google, is to let websites with high MEI scores bypass the no-sound-in-autoplay-content rule. Users can peruse their MSI status by typing chrome://media-engagement into Chrome's address bar.
Chrome 66 also sports some under-the-covers newness, including a trial of "Site Isolation" in preparation for a broader launch later. Site Isolation, which was revealed in December, is a new security technology meant to mitigate risks posed by Spectre, the processor vulnerability sniffed out by Google's own engineers earlier in 2017.
The optional defense - users must manually switch it on - will eventually be made the default in Chrome. But first Google wants to test it on a limited pool of users after addressing earlier issues when it was enabled. Users can decline to participate in the trials by typing chrome://flags/#site-isolation-trial-opt-out in the address bar and then changing "Default" to "Opt-out (not recommended)."
Another big background alteration in Chrome 66 is the move to mark as untrustworthy older digital certificates from Symantec. With its newest version, Chrome labels Symantec-issued certificates generated before June 1, 2016, as insecure. Websites that failed to replace those certificates may be affected as the browser spews messages, some explicit, others subtler, telling users that the connection between them and the destination is insecure, and thus potentially dangerous.
Later this year, Chrome 70 - now set to roll out during the week of Oct. 14-20 - will distrust every Symantec certificate, no matter when it was issued.
The dispute between Google and Symantec over certificates, and Chrome's ban, goes back to 2015, when several browser makers, Google included, accused Symantec and its partners of improperly issuing certificates. Google, for one, concluded that Symantec's problems were endemic.
Google also patched more than 60 security vulnerabilities in version 66, including two marked as "Critical," the most serious ranking in the company's four-step system, and six tagged as "High." The two critical vulnerabilities were reported by researcher Ned Williamson, on March 28 and 30; Google's fast patching was almost certainly due to their seriousness.
Google shelled out $34,000 for reporting 19 of the bugs, with several bounties, including Williamson's, still to be decided.
Chrome's next upgrade, version 67, should start reaching users May 29.
Google on March 6 released Chrome 65 for Windows, macOS and Linux, with fixes for 45 vulnerabilities, and security and developer improvements and enhancements that users won't see, or even notice.
Chrome updates in the background, so users only need relaunch the browser to install the latest version. (To manually update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a "Relaunch" button.) Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks. It last upgraded the browser on Jan. 24.
Some upgrades, like Chrome 64, boast obvious-to-the-end-user modifications that alter the browser's performance, signal adoption of web standards or debut new functionality. (The user interface, or UI, of Chrome has changed little since the browser's 2008 launch.) Other versions - and Chrome 65 is firmly in this camp - make virtually no splash because changes are exclusively behind the scenes, or nearly so.
Tops on that background list is support for the Web Authentication API"enabling the creation and use of strong, attested, scoped, public key-based credentials by web applications, for the purpose of strongly authenticating users." Both Microsoft (for Edge) and Mozilla (Firefox) have also committed to the standard. Support for the API was left disabled in Chrome 65; it can be enabled from the page that results from typing chrome://flags in the address bar.
Other improvements include the introduction of CSS Paint API and Server Timing API. The former lets web developers craft images programmatically, eliminating the need to insert actual images - and thus load a resource from a server - as, say, background. The latter introduces new functionality that site designers and administrators can use to pass performance information on the server, from the server, to the browser.
In other areas, however, Chrome was twiddling thumbs. Last year, Google announced that Chrome 64 would not allow any auto-play content unless the audio was muzzled. Some exceptions were to apply: If the user clicked or tapped (desktop Chrome or mobile Chrome, respectively), "somewhere on the site during the browsing session," the audio would still play. But the mandate did not go live in January with Chrome 64, as expected. Nor has it been activated in Chrome 65. Instead, Google has delayed enforcement to the middle of April, when Chrome 66 will appear.
But sites that have long relied on auto-play content - the sports website espn.com, for one - have been preparing for the Chrome ruling by muting the audio on video clips (the video still cranks up as soon as the user navigates to a story).
Google also patched nearly four dozen security vulnerabilities in version 65, including nine marked as "High," the second-most-serious ranking in the company's four-step system. Google paid researchers $34,500 for reporting 19 of the 45 bugs, with one additional report's bounty still to be decided.
Chrome's next upgrade, to version 66, should start reaching users on April 17.
Google on Jan. 24 released Chrome 64 for Windows, macOS and Linux, boosting the browser's defenses against the microprocessor flaws that blitzed through the news earlier this month.
The upgrade also beefed up Chrome's pop-up blocker, put a stop to hucksters hijacking the browsing session by automatically steering to an unwanted website, and implemented a promised option to let users mute auto-playing audio on a site-by-site basis. And Google's security team patched 53 new vulnerabilities in the browser.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a "Relaunch" button. Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 63, was Dec. 5, or seven weeks ago.
Earlier this month, Google promised to bolster defenses against the Spectre vulnerabilities its Project Zero team had uncovered in most modern processors. The firm followed through with Chrome 64, which boasts a refresh of Google's V8 JavaScript engine. Tweaks to V8 have been added to make it much tougher for hackers to pull off a successful Spectre attack.
Other browser makers beat Google to the punch on Spectre, but the difference appeared to be moot: Active attacks leveraging the vulnerabilities have not appeared, or if they have, been detected.
Chrome 64 included patches for more than four dozen other, more run-of-the-mill vulnerabilities, with Google paying out at least $22,000 in bounties to the researchers who reported the bugs. Google listed some of those bugs here.
Google also continued its war on unwanted and intrusive content by improving Chrome 64's built-in pop-up blocker so that it can handle more kinds of abuses. Devious behavior - including disguising links to third-party websites as an audio/video play control, or as a close-window button - will be spotted by Chrome 64, which will then refuse to open the new tab or window that the criminals had pre-programmed.
Likewise, Chrome 64 sniffs out hidden-to-the-human-eye page elements that auto-open a tab or create a new browser window, then drag the unsuspecting user to a rogue destination. "Usually one of them is an ad or something that you didn't want," Pete LePage, a Google developer advocate, asserted in a post to a company blog. "Starting in Chrome 64, these types of navigations will be blocked, and Chrome will show some native UI [user interface] to the user - allowing them to follow the redirect if they want."
A more noticeable change to Chrome was the adoption of a long-promised option that lets users manually mute auto-play audio on a site-by-site basis.
In September 2017, Google announced that starting with December's Chrome 63, users would be able to select a site-specific muting option from the Page Info bubble (called up by clicking on the "i" within a circle at the far left of the URL in the address bar). Changing the option to "Always block on this site" from "Allow" would silence all auto-play audio on that domain.
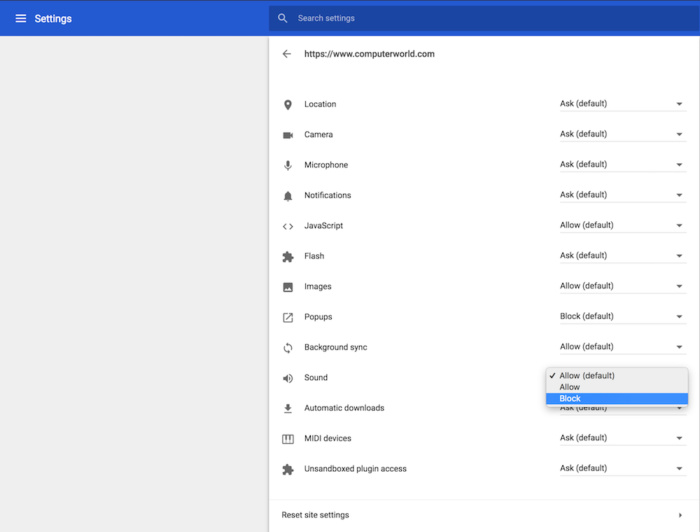
Chrome 64 users can select a site-specific muting option to silence all auto-play audio on that domain.
Google missed the Chrome 63 timeline but managed to bake it into Chrome 64 instead.
However, a more draconian auto-play policy has yet to be put into place. Last year, Google announced that Chrome 64 would not allow any auto-play content unless it muzzled the audio. Some exceptions were to apply: If the user clicked or tapped (desktop Chrome or mobile Chrome, respectively), "somewhere on the site during the browsing session," the audio would still play.
The new keep-it-down-over-there mandate did not go live with Chrome 64, as expected. Instead, Google pushed off the rule's introduction to the middle of April, when Chrome 66 is scheduled to show up.
Google's next browser upgrade, Chrome 65, should reach users the week of March 4-10, according to its release calendar.
Google this week issued Chrome 63 for Windows, macOS and Linux, adding important security enhancements for enterprises to stress the importance the company now puts on the commercial market.
"Starting with [this] release, Site Isolation is now available ... [which] renders content for each open website in a separate process, isolated from other websites. This can mean even stronger security boundaries between websites than Chrome's existing sandboxing technology," wrote Matt Blumberg, product manager for Chrome, in a post to a company blog.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a "Relaunch" button. New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 63, was Oct. 17, or seven weeks before its Wednesday refresh.
Although Chrome 63 includes improvements aimed at all users - such as a speedier V8 JavaScript engine - Google chose to trumpet a number suitable only for corporate customers.
The most prominent is the Site Isolation Blumberg discussed. When enabled, the feature and its underlying technologies render each open website in a separate, dedicated process, isolating that site - and more importantly, its contents - from other sites. A major step up from the already-in-Chrome by-tab process assignments, site isolation will prevent remote code that does execute within Chrome's renderer sandbox from manipulating other sites, and the code within them.
The new quarantine is more rigid than Chrome's current sandboxing. According to Google, while Chrome now "makes an effort to place pages from different websites in different renderer processes when possible," that doesn't always happen. Site Isolation guarantees that each site is separated from all others.
It also comes at a price: Google acknowledged that turning on Site Isolation will increase Chrome's memory usage up to 20%, a tough penalty when users already bemoan the browser's voracious appetite.
Site Isolation can be enabled for all sites, or just a select few - a company's intranet, for example - or other internal websites that contain the most sensitive information and are thus the most valuable to hackers, like customer data.
Windows GPOs - Group Policy Objects - can be set by administrators and then pushed to those workers running Chrome. Command-line flags can also be used on individual machines or for IT testing prior to wider deployment via group policies. Instructions are available here.
Google isn't the only browser maker trumpeting isolationist technologies. Chrome may have led the way to multiple processes - it debuted in 2008 with that in place - and historically been the most difficult of the major browsers to crack and hack, but Microsoft has expended time and money on its Edge, too. The latest move by Microsoft - Application Guard, baked into Windows 10 - isolates Edge in a bare bones virtual machine; it cannot be duplicated by Google.
Also on the Chrome 63 change list: GPOs that the IT staff can set to bar Chrome extensions by the privileges they demand. For example, the new policies could be used to ensure users don't install any add-on that can capture audio through a device's microphone or access the company's printers. The upgrade also turns on TLS (Transport Layer Security) 1.3, a more robust encryption standard, when Chrome is steered to gmail.com. Blumberg promised that TLS 1.3 support would expand "to the broader web" in 2018.
Blumberg also issued one of Google's periodic advance warnings about future moves meant for Chrome, telling users that come version 68 - slated to ship the week of July 22-28, 2018 - Google will start blocking third-party software from injecting code into Chrome on Windows. Antivirus (AV) applications in particular use code-injection, a now-disparaged technique because of stability issues and vulnerability to hackers' attacks, to monitor browsers for possible infection.
With version 68, only software that, if banned from injecting code into Chrome, crashes the browser will be allowed to run so that Chrome can launch and display a message advising the user to remove the culprit. When Chrome 72 launches in early 2019, all code injection will be stymied. However, recognizing that enterprises may be wedded to such software, and unable to abandon those programs or find substitutes, Google plans to introduce GPOs that "offer admins extended support for critical apps" requiring code injection.
Included in Chrome 63 are patches for 37 security flaws, one of which was rated "Critical," Google's most-serious, and rare, ranking. That bug's finder was awarded $10,500 for his report, with more than $36,000 in bounties paid to security researchers for the remaining vulnerabilities.
The next upgrade, Chrome 64, should reach users the week of Jan. 21-27, 2018, according to Google's release calendar.
Google this week released Chrome 62 for Windows, macOS and Linux, setting the stage for a new warning when users enter data on an unencrypted website and patching nearly three dozen security vulnerabilities.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. (To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a "Relaunch" button.) New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 61, was Sept. 6, or just under six weeks before its Tuesday refresh.
Version 62, like most of Chrome's upgrades, hands over few if any obvious-at-a-glance changes. An exception this time: Chrome 62 is now ready to alert users that a site is insecure if it a) isn't encrypted with a digital certificate and b) the user starts to fill out any form field on the page. Also set to receive warnings are all pages viewed in Chrome's "Incognito" mode, the browser's no-tracks session. In those scenarios, users will see the text "Not Secure" at the far left of the address bar.
The feature is "now ready" because as of Friday, Google had not switched on the alert. That wasn't a surprise: Google typically tests a new feature with a small fraction of the total Chrome user base before remotely enabling the feature for all users. Assuming that feedback and Google's own telemetry point to zero problems, it will flip a flag and the warnings will appear.
Those who want to see the warning immediately should enter chrome://flags in the address bar, search for and find the entry "Mark non-secure origins as non-secure," and change the entry in the drop-down list from "Default" to "Warn on HTTP while in incognito mode or after editing forms."
The Not Secure warning is the latest step in an extended process that Google has aggressively implemented - mainly using Chrome, but with other services in its stable, too, like Gmail - to pressure all sites to encrypt their traffic. Chrome already sounded the alarm when an unencrypted site accepted passwords or credit card information; 62 is the next in the planned progression.
Eventually, Chrome will show the Not Secure notice on every HTTP page.
Also on the Chrome 62 change list are support for OpenType variable fonts, which compact multiple font sizes and styles in a single package, giving site designers more flexibility in crafting attractive pages; and support for an expanded Network Information API (application programming interface) that provides connection performance metrics from the browser, a useful tool for web app developers creating software suitable for a variety of speeds.
Included in Chrome 62 are patches for 35 security vulnerabilities, a fifth of which were rated "High," Google's second-most-serious ranking. The firm paid out just over $40,000 in bug bounties to security researchers for reporting the vulnerabilities.
The next upgrade, Chrome 63, should reach users the week of Dec. 3-9, according to Google's release calendar.
Chrome automatically downloads its latest update in the background, then refreshes itself the next time it's launched.
Google on Wednesday released Chrome 61 for Windows, macOS and Linux, adding several new behind-the-scenes features -- including one that lets web apps access USB peripherals -- and patching 22 security vulnerabilities.
Chrome updates in the background, so most users need only relaunch the browser to get the latest version. (To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a "Relaunch" button.) New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 60, was July 25, or just over six weeks ago.
Version 61, like many if not most of Chrome's upgrades, deals users few if any changes they'll notice at a glance. Instead, this month's update offers new under-the-hood functionality aimed at site and app developers.
Near the top of that change list is the WebUSB API (application programming interface), which is intended to give web app and site developers access to unusual USB devices.
"Most hardware peripherals such as keyboards, mice, printers, and gamepads are supported by high-level web platform APIs," Pete LePage, a developer advocate at Google, noted in a post about Chrome 61. "But, using specialized educational, scientific, industrial or other USB devices in the browser has been hard, often requiring specialized drivers."
And Chrome 61 added native support for JavaScript modules so developers can properly call up discrete and reusable chunks of script code from within the browser without performing a build step. Chrome's support - like that already baked into Apple's Safari browser - allows for fetching dependent modules in parallel, and guarantees that the script executes in the right order. Mozilla and Microsoft plan to natively support JavaScript modules in their Firefox and Edge browsers down the road.
Additionally, Chrome will now automatically drop out of full-screen mode if a JavaScript dialog box opens; scammers often use such dialogs, and a forced shift to full-screen, to prevent the user from discarding their bogus claims of PC infections.
Also included in Chrome 61 are patches for 22 security vulnerabilities, a quarter of which were rated "High," Google's second-most-serious ranking. The firm also paid out $23,500 in bug bounties - and will pay more once it decides how much to fork over for one of the flaws - to security researchers for reporting the vulnerabilities.
Although it didn't tie it to the release of Chrome 61, Google also recently made it possible for users to install browser previews alongside the stable, production-grade version on a Windows personal computer. The Beta and Dev channel builds can be downloaded from here.
The next edition, Chrome 62, should reach users the week of Oct. 15-21, according to Google's release calendar.
Chrome updates automatically in the background, then upgrades itself the next time it's launched.
Chrome 60 update (July 25, 2017)
Google on Tuesday released Chrome 60 for Windows, macOS and Linux, adding support for the Touch Bar on the newest MacBook Pro laptops and a new online payment API, and patching 40 security vulnerabilities.
Chrome updates in the background, so most users need only relaunch the browser to get the latest version. (To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser is already up to date or displays the updating process before presenting a "Relaunch" button.)
The Mountain View, Calif. company updates Chrome every six or seven weeks; the last time it upgraded the browser, to version 59, was June 5, or just over seven weeks ago.
Much of Chrome 60's new features and functional changes are under the hood, aimed exclusively at website and app developers. One exception: Support for the MacBook Pro Touch Bar.
In October 2016, and on the top-end 13- and 15-in. models, Apple replaced the static row of function keys at the top of the MacBook Pro keyboard with an OLED (organic light-emitting diode) display whose contents change depending on the active application. Initially, Touch Bar support came from Apple and its own software, such as Maps. A few third-party programs, including Adobe Photoshop and Microsoft Office, have followed suit.
Apple's own browser, Safari, supported the Touch Bar out of the gate last year.
[ To comment on this story, visit Computerworld's Facebook page. ]
Now, when Chrome is the active application, the Touch Bar displays Chrome-specific virtual buttons, like those for moving forward and backward through browsing history, refreshing the current web page or bookmarking it. Users can customize the Touch Bar settings for Chrome from within the browser.
Google added a host of developer-only features and APIs (application programming interfaces) to Chrome 60, notably support for the already existing Payment Release API, which is designed to simplify online payments by eliminating the traditional check-out forms many websites use. Currently, Chrome, Microsoft's Edge and Mozilla's Firefox all support the API, although the latter has disabled it in current builds.
Also included in Chrome 60 were patches for 40 security vulnerabilities, nearly a quarter of which were rated "High," the second-most-serious ranking in Google's four-step system. Google paid out $26,000 in bug bounties -- and will pay more than that in the end, as it has yet to decide on three of the vulnerabilities -- to security researchers for reporting the flaws.
People who haven't tried Google's desktop browser can download Chrome 60 for Windows, macOS Linux from Google's website. Current users can let the automatic updater download and install the new version. To manually trigger the pending update, users select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right.
The next edition, Chrome 61, should reach users the week of Sept. 3-9, according to Google's release calendar.
Chrome 60 update (July 25, 2017)
Google on Tuesday released Chrome 60 for Windows, macOS and Linux, adding support for the Touch Bar on the newest MacBook Pro laptops and a new online payment API, and patching 40 security vulnerabilities.
Chrome updates in the background, so most users need only relaunch the browser to get the latest version. (To manually manage an update, select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser is already up to date or displays the updating process before presenting a "Relaunch" button.)
The Mountain View, Calif. company updates Chrome every six or seven weeks; the last time it upgraded the browser, to version 59, was June 5, or just over seven weeks ago.
Much of Chrome 60's new features and functional changes are under the hood, aimed exclusively at website and app developers. One exception: Support for the MacBook Pro Touch Bar.
In October 2016, and on the top-end 13- and 15-in. models, Apple replaced the static row of function keys at the top of the MacBook Pro keyboard with an OLED (organic light-emitting diode) display whose contents change depending on the active application. Initially, Touch Bar support came from Apple and its own software, such as Maps. A few third-party programs, including Adobe Photoshop and Microsoft Office, have followed suit.
Apple's own browser, Safari, supported the Touch Bar out of the gate last year.
Now, when Chrome is the active application, the Touch Bar displays Chrome-specific virtual buttons, like those for moving forward and backward through browsing history, refreshing the current web page or bookmarking it. Users can customize the Touch Bar settings for Chrome from within the browser.
Google added a host of developer-only features and APIs (application programming interfaces) to Chrome 60, notably support for the already existing Payment Release API, which is designed to simplify online payments by eliminating the traditional check-out forms many websites use. Currently, Chrome, Microsoft's Edge and Mozilla's Firefox all support the API, although the latter has disabled it in current builds.
Also included in Chrome 60 were patches for 40 security vulnerabilities, nearly a quarter of which were rated "High," the second-most-serious ranking in Google's four-step system. Google paid out $26,000 in bug bounties -- and will pay more than that in the end, as it has yet to decide on three of the vulnerabilities -- to security researchers for reporting the flaws.
People who haven't tried Google's desktop browser can download Chrome 60 for Windows, macOS Linux from Google's website. Current users can let the automatic updater download and install the new version. To manually trigger the pending update, users select "About Google Chrome" from the Help menu under the vertical ellipsis at the upper right.
The next edition, Chrome 61, should reach users the week of Sept. 3-9, according to Google's release calendar.
Read the original article on computerworld.com.
More about: Chrome
















































